Virtual CISO Services
Protect Your Organization with a Virtual CISO
A Competitive Advantage
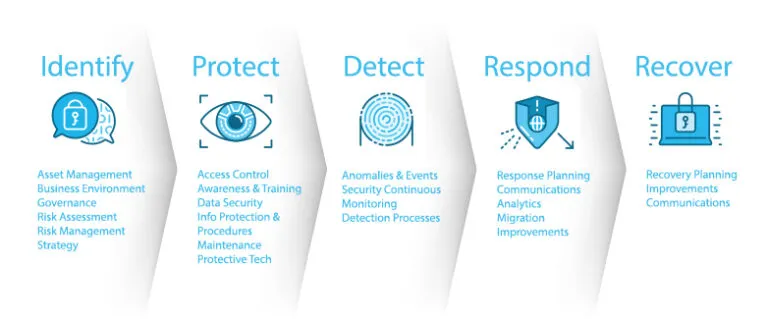
Under its “Fractional CISO” services grouping, OCD Tech offers a retainer-based approach to assisting organizations extend the capabilities of their information security team. By leveraging OCD Tech for this service, you get access to a team of experts at a cost much less than one full-time employee. We take an inclusive approach to this type of service, bundling a wide variety of services to help you secure your organization. OCD Tech’s capabilities extends organizations’ ability to address common security needs, represented by NIST’s “Five Factors”.
Access to Our Expertise
This time can be used for whatever purpose the organization sees fit. In other engagements with this time, we have:
Performed information security maturity assessments
Helped organizations prioritize and roadmap security initiatives
Written policies and procedures to address gaps or regulatory concerns
Performed security incident triage
Written incident runbooks for front-line IT staff
Organized proof of concepts for new security tools
Written RFPs on behalf of our clients for things like Mobile Device Management and SIEM, among others
Creating policies and procedures is a vital part of maintaining an effective cybersecurity program. Establishing common themes, goals, standards, and benchmarks helps to set organizations on a uniform course towards IT governance. As part of the vCISO offering, OCD Tech will help your organization create and maintain the IT security policies and procedures that govern your IT security program.
Use Existing Policies
Use Policy Templates
Creating Policies from Scratch
Maintaining Policies
Regulatory Obligations
In addition to best practice, OCD Tech will make all recommendations on your IT environment with those regulations in mind. This includes building polices which often will be key in your compliance programs.
Common regulatory obligations include:
MA 201 CMR 17
NY SHIELD
FTC Safeguards Rule
AICPA SOC 2
ISO 27001
No matter the regulation(s) that your organization is obligated to, OCD Tech will help to create an IT security program that aligns with the requirements. When necessary, OCD Tech will help to create controls that are measurable and repeatable in support of these regulations.



.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)