SOC 2® Readiness Assessment
SOC 2® Readiness Assessment Process
OCD Tech has significant experience conducting SOC 2® readiness assessments for companies across multiple industries. Our seasoned professionals have deep technical expertise which is augmented by years of practical experience working with management to identify issues and implement remediation steps. The result is both peace of mind and confidence about the company’s ability to meet SOC 2® requirements.
- Processing Integrity, ensuring that system processing is accurate, complete, and authorized.
- Identifying areas requiring improvement.
- Enhancing the organization’s ability to manage cybersecurity risks.
Our Readiness Assessment Service
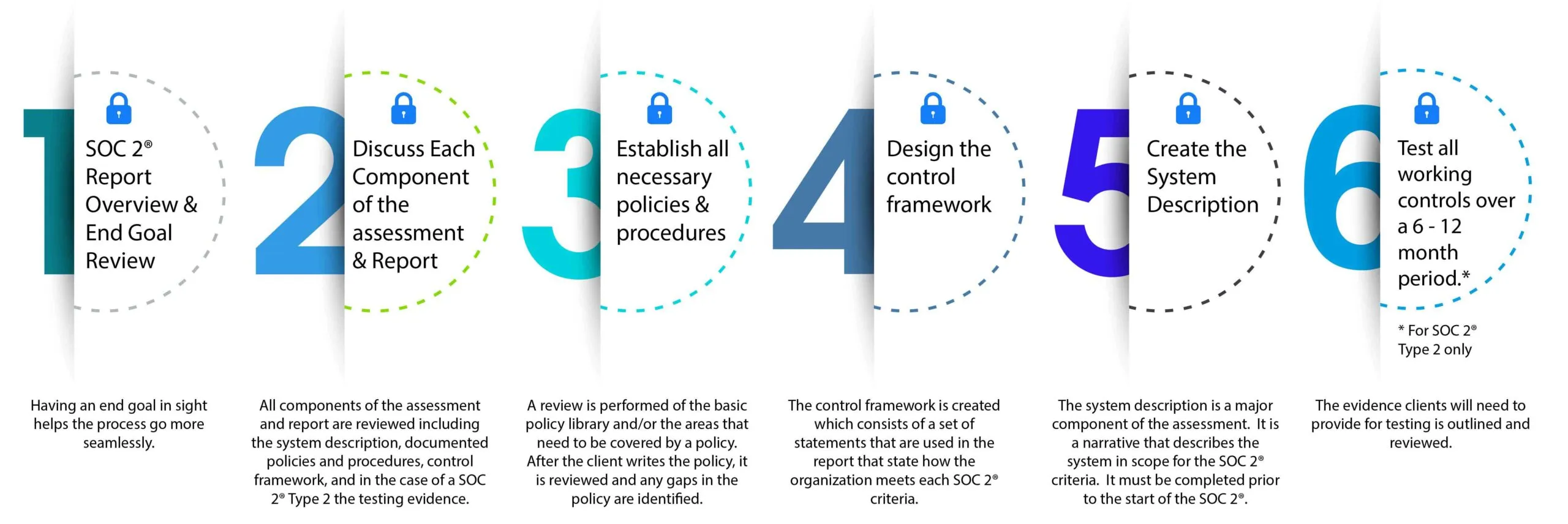
- SOC 2® Report Overview – Having an end goal in sight helps the process go more smoothly.
- Discuss Each Component of the Assessment – All components of the assessment and report are reviewed including the system description, documented policies and procedures, control framework, and testing evidence.
- Establish Policies & Procedures – A review is performed of the basic policy library and/or the areas that need to be covered by a policy. It is reviewed and any gaps in the policy are identified.
- Design the Control Framework – The framework is created which consists of a set of statements that are used in the report that highlight how the organizations meets each SOC 2®
- Create the System Description – The system description is a major component of the assessment. It is a narrative that describes the system in scope for the SOC 2® It must be completed prior to the start of the SOC 2® exam.
- Test Working Controls – The evidence that organizations will need to provide for testing is identified and reviewed.


.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)