Privileged Access Management
Privileged Access Management Audit
& Compliance Services
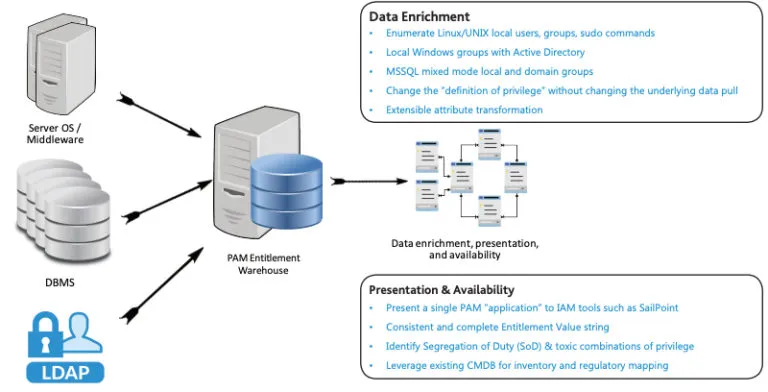
OCD Tech has identified a critical gap in the overall Identity Access Management (IAM) control landscape. The deficiency lies in the ability to see the most important and privileged accounts, the system administrators.
- Local Microsoft Windows
- Duplicate UNIX/Linux UID / GID membership
- Sudo access
- Inside MSSQL, Oracle, DB2, SyBase, Postgres databases



.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)