Network Penetration Testing
Keep Your Organization Secure with our Penetration Testing Services
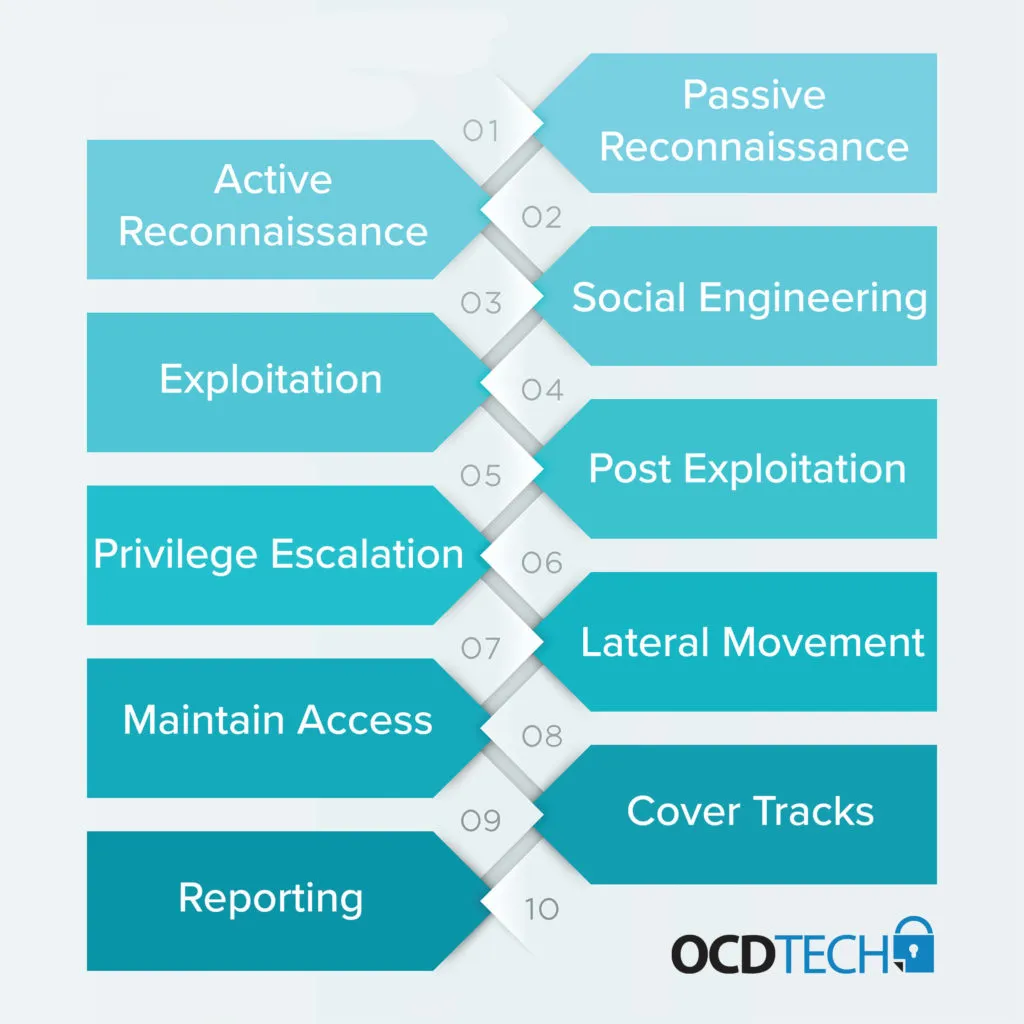
The methodology presented below is broad, and a carefully defined scope will drive the actual components of the test. The penetration test, in general, includes the following components:
- Passive Reconnaissance
Leverage sources of Open Source Intelligence to collect information about the organization and its employees.
- Active Reconnaissance
Characterize the target network and target systems to identify potentially exploitable vulnerabilities or misconfigurations.
- Social Engineering
Target end-users in an attempt to recover sensitive information or install malicious software. This can take several forms.
- Exploitation
Gain unauthorized access to target systems.
- Post Exploitation
Use the newly established foothold to gather information specific to the level of privilege gained that was previously not available.
- Privilege Escalation
Gain administrator-level access to target systems.
- Lateral Movement
Leverage collected data to move throughout the network, with a focus on obtaining access to critical systems.
- Maintain Access
Depending on the scope of the test, ensure that compromised systems may be accessed throughout the test.
- Cover Tracks
Depending on the scope of the test, ensure that all traces of attacker activity are removed.
- Reporting
Compile all information gathered during the penetration test for management.


.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)