By
OCD Tech
June 10, 2020
•
2
min read
The path towards Cybersecurity Maturity Model Certification (CMMC) for Department of Defense (DoD) contractors handling Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) has been clearly defined by the CMMC-Accreditation Body (CMMC-AB):
Be sure to utilize the (draft) Glossary of terms posted on the CMMC-AB website while conducting your research. Learning these terms will simplify any future assessment and/or certification efforts.
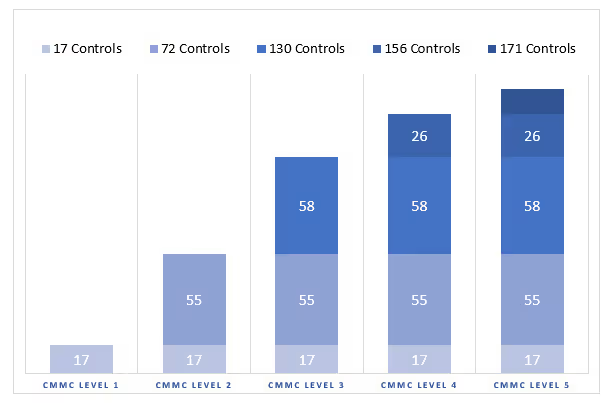
Defense Industrial Base (DIB) organizations that have accurately self-attested their compliance with the DFARS 7012 standard will have already implemented 110 of the 130 controls required to achieve CMMC Level 3 certification. The additional 20 controls (or GAP Controls) that must be implemented are:
AM.3.036. Define procedures for the handling of CUI data.
AU.3.048. Collect audit logs into a central repository.
AU.2.044. Review audit logs.
IR.2.093. Detect and report events.
IR.2.094. Analyze and triage events to support event resolution and incident declaration.
IR.2.096. Develop and implement responses to declared incidents according to pre-defined procedures.
IR.2.097. Perform root cause analysis on incidents to determine underlying causes.
RE.2.137. Regularly perform and test data back-ups.
RE.3.139. Regularly perform complete and comprehensive data back-ups and store them off-site and offline.
RM.3.144. Periodically perform risk assessments to identify and prioritize risks according to the defined risk categories, risk sources, and risk measurement criteria.
RM.3.146. Develop and implement risk mitigation plans.
RM.3.147. Manage non-vendor-supported products (e.g., end of life) separately and restrict as necessary to reduce risk.
CA.3.162. Employ code reviews of enterprise software developed for internal use to identify areas of concern that require additional improvements.
SA.3.169. Receive and respond to cyber threat intelligence from information sharing forums and sources and communicate to stakeholders.
SC.2.179. Use encrypted sessions for the management of network devices.
SC.3.192. Implement Domain Name System (DNS) filtering services.
SC.3.193. Implement a policy restricting the publication of CUI on publicly accessible websites (e.g., Forums, LinkedIn, Facebook, Twitter, etc.).
SI.3.218. Employ spam protection mechanisms at information system access entry and exit points.
SI.3.219. Implement DNS or asymmetric cryptography email protections.
SI.3.220. Utilize email sandboxing to detect or block potentially malicious email attachments.
Echoing the recommendation of the CMMC-AB, we strongly encourage DIB organizations begin conducting proactive CMMC Readiness exercises. Working with OCD Tech to assess your organization against the current (NIST 800-171) and future (CMMC) standards will bring you up to date with the existing requirements while simultaneously positioning your organization to successfully achieve CMMC certification.
Contact Us

Audit. Security. Assurance.
IT Audit | Cybersecurity | IT Assurance | IT Security Consultants – OCD Tech is a technology consulting firm serving the IT security and consulting needs of businesses in Boston (MA), Braintree (MA) and across New England. We primarily serve Fortune 500 companies including auto dealers, financial institutions, higher education, government contractors, and not-for-profit organizations with SOC 2 reporting, CMMC readiness, IT Security Audits, Penetration Testing and Vulnerability Assessments. We also provide dark web monitoring, DFARS compliance, and IT general controls review.
Contact Info
.svg)
OCD Tech
.svg)
25 BHOP, Suite 407, Braintree MA, 02184
.svg)
844-623-8324
.svg)
https://ocd-tech.com
Follow Us
Videos
Check Out the Latest Videos From OCD Tech!
Services
SOC Reporting Services
– SOC 2 ® Readiness Assessment
– SOC 2 ®
– SOC 3 ®
– SOC for Cybersecurity ®
IT Advisory Services
– IT Vulnerability Assessment
– Penetration Testing
– Privileged Access Management
– Social Engineering
– WISP
– General IT Controls Review
IT Government Compliance Services
– CMMC
– DFARS Compliance
– FTC Safeguards vCISO