By
Michael Hammond
August 2, 2016
•
4
min read
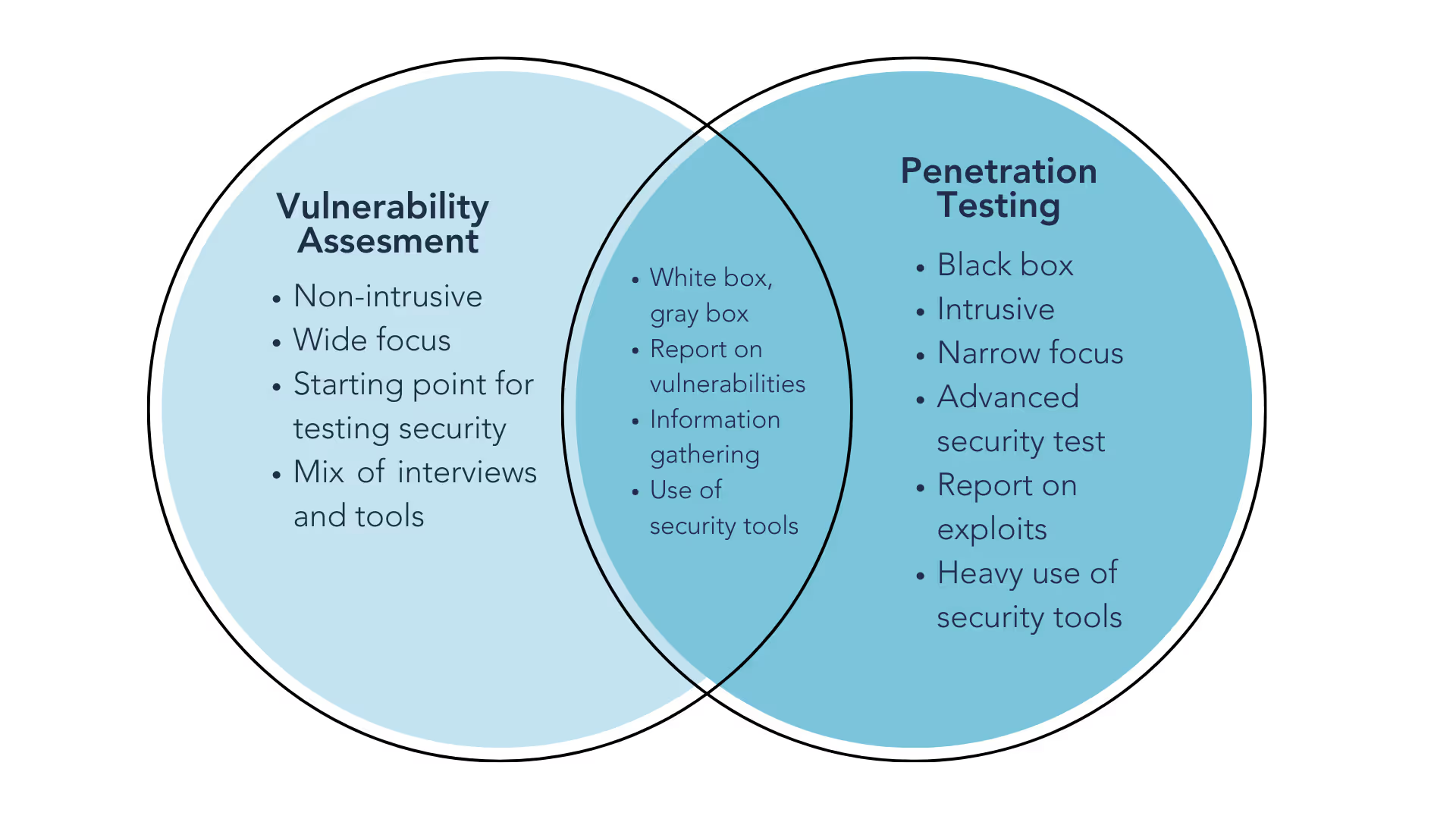
In the world of IT Security, one question consistently rises to the top: Vulnerability Assessment vs. Penetration Testing—which one do you need to keep your organization safe? For those new to the field, IT Security can be daunting, filled with endless jargon and technical complexities. Non-technical executives and managers may wonder where to start, whether to hire consultants, and which specific services are necessary. It’s critical to understand the distinction between these two approaches before you invest in any security solution.A vulnerability assessment is the process of examining your organization’s people, process, and technology, for the purpose of identifying weaknesses. We use a mixed approach of interviews with key staff as well as the use of technical security tools to examine the network and connected devices. Typically, the engagement ends with a report showing vulnerabilities with recommendations on how to fix them.Penetration testing refers to the attempt to identify - and crucially exploit - vulnerabilities in systems for the purpose of breaching a company’s defenses. A penetration test can be an extension of a vulnerability assessment. A penetration test can take a few different forms, white box, black box, or gray box. Generally, the color implies the amount of information the tester knows beforehand. A white box test may follow a vulnerability assessment. That is to say, the penetration tester will have detailed knowledge of the company, its network, and the system in question. A black box approach would involve very little information being given to the tester beforehand, beyond a scope and terms of engagement. As you might have guessed, gray box is a hybrid approach.The engagement typically ends with a report, detail on how the particular systems were breached, and advice on how best to secure the network or applications against the exploited vulnerabilities.When considering Vulnerability Assessment vs. Penetration Testing, keep in mind that vulnerability assessments represent a wide focus, designed to assess an organization from end to end. Often, they are considered a starting point for companies with a maturing security culture. Penetration testing, on the other hand, is a narrower, more targeted engagement—typically focusing on one system or one network segment—and is typically undertaken by organizations with a mature security posture, looking to harden key systems against advanced attacks.Further Reading
If you have any questions on IT Security matters, please contact our team of professionals at OCD Tech.

Audit. Security. Assurance.
IT Audit | Cybersecurity | IT Assurance | IT Security Consultants – OCD Tech is a technology consulting firm serving the IT security and consulting needs of businesses in Boston (MA), Braintree (MA) and across New England. We primarily serve Fortune 500 companies including auto dealers, financial institutions, higher education, government contractors, and not-for-profit organizations with SOC 2 reporting, CMMC readiness, IT Security Audits, Penetration Testing and Vulnerability Assessments. We also provide dark web monitoring, DFARS compliance, and IT general controls review.
Contact Info
.svg)
OCD Tech
.svg)
25 BHOP, Suite 407, Braintree MA, 02184
.svg)
844-623-8324
.svg)
https://ocd-tech.com
Follow Us
Videos
Check Out the Latest Videos From OCD Tech!
Services
SOC Reporting Services
– SOC 2 ® Readiness Assessment
– SOC 2 ®
– SOC 3 ®
– SOC for Cybersecurity ®
IT Advisory Services
– IT Vulnerability Assessment
– Penetration Testing
– Privileged Access Management
– Social Engineering
– WISP
– General IT Controls Review
IT Government Compliance Services
– CMMC
– DFARS Compliance
– FTC Safeguards vCISO