Mitigating Social Engineering Threats
66% OF SECURITY COMPROMISES ARE THE RESULT OF EMPLOYEE ERROR!
Social Engineering involves the psychological manipulation of people to disclose critical information about themselves or their companies. This manipulation often involves confidence tricks, or “cons” to deceive the mark. The field of social engineering comprises.
OCD Tech offers Social Engineering services to clients. Our approach consists of impersonating would-be hackers, sending deceptive emails to your staff, attempting to get them to click links and download attachments.
OCD Tech specializes in making sure employees understand the mechanisms of spam, phishing, spear-phishing, malware, and social engineering. You get high quality web-based interactive training combined with common traps, live demonstration videos, short comprehension tests, and scenario-based Danger Zone exercises. When it comes to rolling out training for your users, our platform’s Automated Training Campaigns do the heavy lifting for you.
GAIN INSIGHT INTO YOUR ORGANIZATION AND ITS USERS WITH OUR FREE TOOLS!
Social Engineering Phishing Test
OCD Tech’s highly effective scheduled Phishing Security Tests keep your employees on their toes with security top of mind. Within the Admin Console, you are able to schedule regular Phishing Security Tests from our large library of known-to-work templates or choose a template from the community templates section where you can also share phishing templates with your peers.
We provide baseline testing to assess your phish-prone staff.
On-demand, interactive, engaging training with common traps and live demos.
Fully automated simulated phishing attacks and hundreds of templates with unlimited usage.
Enterprise-strength reporting, showing stats and graphs for both training and phishing, ready for management.
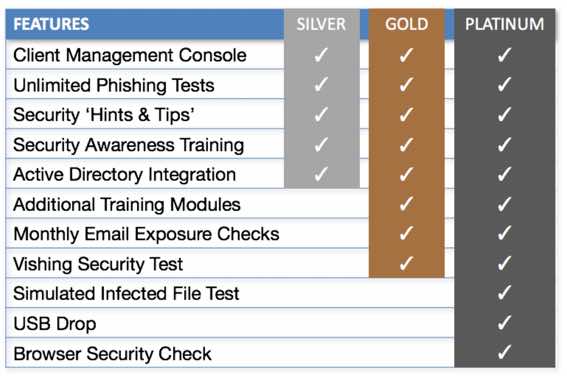
Social Engineering Service Tiers
All of the services listed in the table are available for a full year, on an ongoing basis. The number, frequency, and type of tests cam be customized based on client needs. We provide three distinct service tiers, which vary based on the level of testing and training required.
HOW DOES OCD TECH’S SOCIAL ENGINEERING PLATFORM WORK?
Our pricing is roughly based upon the number of seats and the tier of service desired, though we also factor in the time and effort required to complete the engagement.
We offer both online and in-person training. Contact us for a custom quote that’s tailored to your needs.
Vishing is the act of using a telephone to attempt to scam or cheat an individual into giving up private information.
- Our online platform does a lot of the heavy lifting for you.
- On-demand, browser-based training featuring “The World’s Most Famous Hacker”
- Multiple awareness training modules available
- Create multiple training campaigns as ongoing or with a specified completion date
- Automated enrollment and follow-up emails to ‘nudge’ users who have not completed their training
- Auto-enroll new users added to a group or company
- Point-of-failure training auto-enrollment
- Dedicated Hosting Options, or run the course in your own LMS
Our hosted platform offers a number of approaches and templates that can be used in simulated phishing attacks. Some of the features of our platform include:
- Unlimited year-round simulated phishing attacks
- Full library of successful phishing templates
- Easily create your own templates
- Customizable landing pages
- Customizable “hover-links” when a user mouses over
- Tests for opening MS Office attachments and secondary action of enabling macros
- Set-it-and-forget-it scheduling of attacks and campaign length
- “Anti-Prarie dog” campaigns that send random templates at random times preventing users warning each other
- Phish Alert Outlook add-in button gives your users a way to report simulated and non-simulated phishing attacks
- Vishing Security Tests using IVR attacks over the phone
