Week 2: October 10-14, 2016 – Topic: Cyber from the Break Room to the Board Room We are all part […]
We promised to write about the tools of our trade. A few of the services we perform, whether it’s Vulnerability Assessment […]
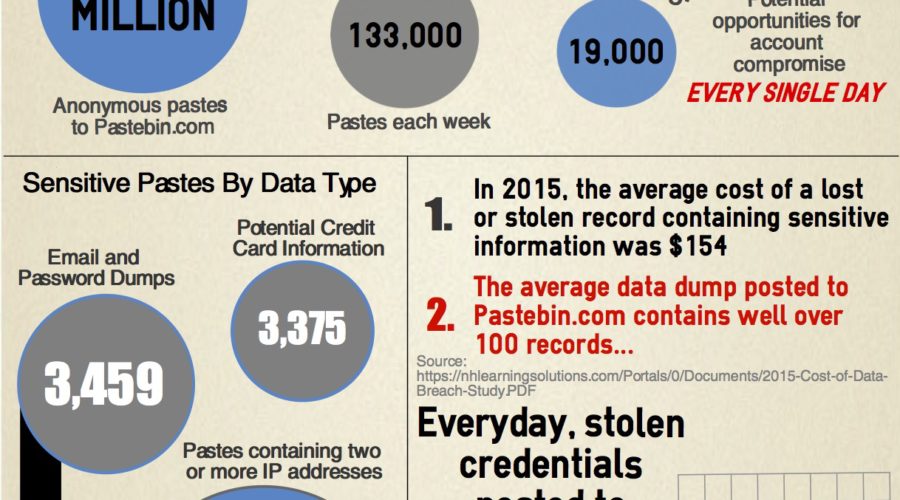
IT Audit & Security testing is a hot topic lately. With the reoccurrence of cyberattacks discussed by the media, and […]
What if there was a way to identify future attacks on a company just by reading publicly available sources on […]
On December 6th, 2016, two members of our team, Nick DeLena, Senior Manager and W. Jackson Schultz, Senior IT Audit […]
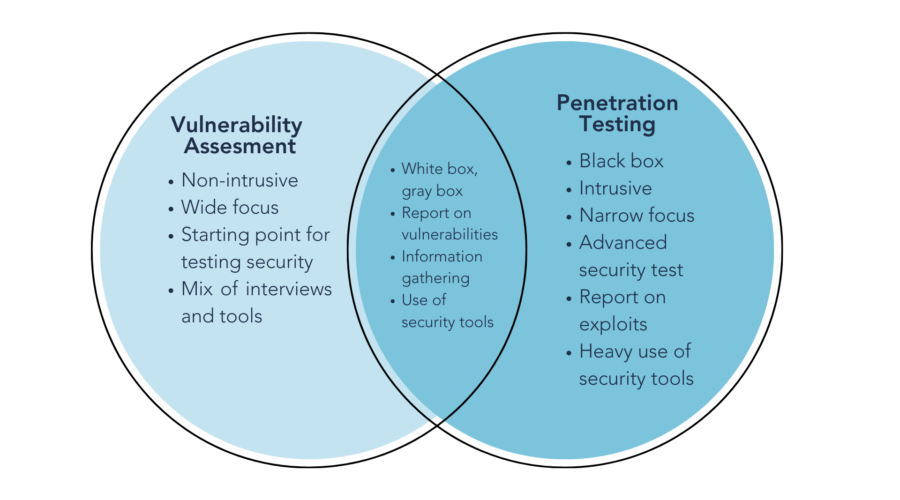
Vulnerability Assessment vs. Penetration Testing
In the world of IT Security, one question consistently rises to the top: Vulnerability Assessment vs. Penetration Testing—which one do you […]
In Case You Missed It – CEO Fired After Wire Transfer Scam Results in $47 Million (USD) in Losses In […]
The Most Vulnerable – Smartphones
Pokemon Go is just the latest example in a growing list of smartphone security breaches. It has been reported that […]
In a landscape-shaping turn of events, the first HIPAA Business Associate has been required to face and pay a $650,000 […]
Featured in the May 2016 Massachusetts State Automobile Dealers Association (MSADA) Magazine (www.msada.org) From the corner window of your office, the front of […]