Federal agency reveals the first group of winners from its six-year competition. The U.S. Department of Commerce’s National Institute of […]
On August 4, 2023, the SEC’s cybersecurity disclosure rules were published in the Federal Register. The Securities and Exchange Commission […]
5 Ways to Enhance Cloud Security and Protect Against Threats As businesses increasingly rely on cloud computing, it’s important to […]
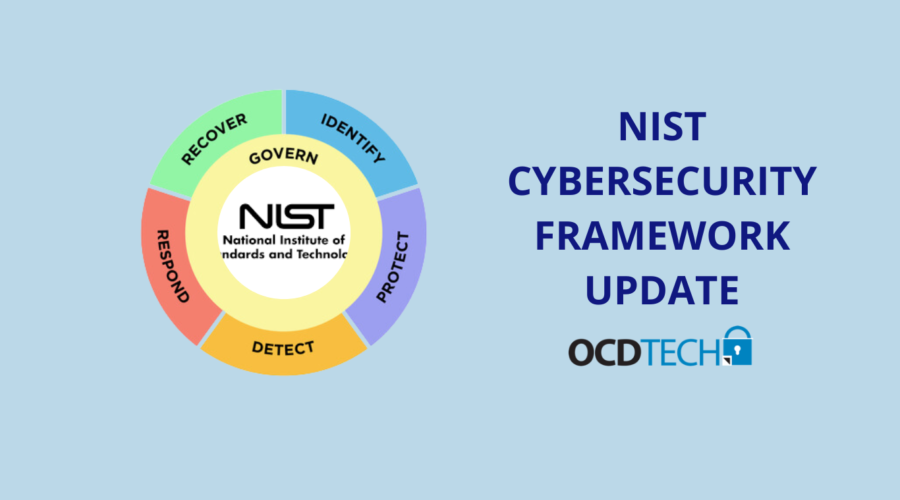
NIST Framework update
The National Institute of Standards and Technology (NIST) has recently released the draft of Cybersecurity Framework 2.0, providing organizations with […]
Benefits of Using a VPN
Why You Should Start Today Online privacy has become a major concern for many individuals. One effective tool in safeguarding […]
On July 31st, the Biden-Harris Administration unveiled the National Cyber Workforce and Education Strategy (NCWES), a first-of-its-kind comprehensive approach aimed […]
The Importance of Implementing a USB Usage Policy in the Workplace Data breaches and unauthorized access to sensitive information are […]
5 Ways the World Wide Web Has Changed Our Lives World Wide Web Day is a celebration of the internet […]
The Hidden Threat In today’s digital age, it’s not just our computers and smartphones that are at risk of cyber […]
Building a Strong Cyber Resilience Strategy: Tips and Best Practices for Businesses Businesses of all sizes and industries face an […]