With Crypto, Most Bugs and Quicks are Preventable
As with any “new” technology, there are always bugs and quirks, but unfortunately in the crypto world they are happening more and more. The worst part, many of them are preventable and are caused by the age-old problem: the user. While I will share this most recent scam that went around, you first must understand where it stems from.
If you stay up to date on what is happening in crypto, you probably know about the recent OpenSea issue, where millions worth of NFTs (Non-Fungible Tokens) were bought at ridiculously low prices. For those that don’t know, here is what happened: OpenSea allows users to list an NFT for free. Once the user approves an NFT collection for sale with a token approval, listings only require a signature thereafter. However, if you want to cancel said listing, it requires an on-chain transaction which costs gas fees to write to the blockchain. Without going into too much detail, gas refers to the unit that measures the amount of computational effort required to execute specific operations on the Ethereum network. Since each Ethereum transaction requires computational resources to execute, each transaction requires a fee. Gas refers to the fee required to conduct a transaction on Ethereum successfully. It is important to note that OpenSea stores listings and offers in an off-chain database to save users gas fees. Therefore, listings and offers only require a signature.
Savvy users discovered a workaround where they were able to avoid paying the cancellation fee. This was accomplished by transferring the NFT to another wallet. Since the NFT no longer existed in the original wallet that signed the listing, all listings pertaining to that would essentially be rendered invalid and automatically removed from OpenSea’s website.
When an NFT with active listings is transferred, the listings disappear from the OpenSea website, but remained in the aforementioned database. These listings remain active until their expiration dates and can be accessed through OpenSea’s API. If an NFT is subsequently transferred back into the original wallet, the old listings can be used to purchase the item. And that’s exactly what happened in January. A malicious actor utilized a vulnerability in the backend of OpenSea (via API) to buy NFTs at old non-expired listing prices that did not show on the front end (website) as being active anymore.
More then 57 ETH ($137k at the time) worth of sales went through on high end NFTs at prices well below the NFT collection floor price. A collections floor price is equal to the cheapest listed NFT in that collection. The stolen NFTs were instantly listed for sale just below the floor price of each collection in order to make for a quick sale. All of them sold for approximately 390 ETH ($936k) netting a profit for the scammer of $700k.
Due to this exploit, OpenSea spent the last few weeks developing a new smart contract to prevent this from happening in the future. With the new contract, users will be required to migrate their existing listings to the new smart contract. OpenSea communicated this via emails to users, giving them a week to migrate their listings.
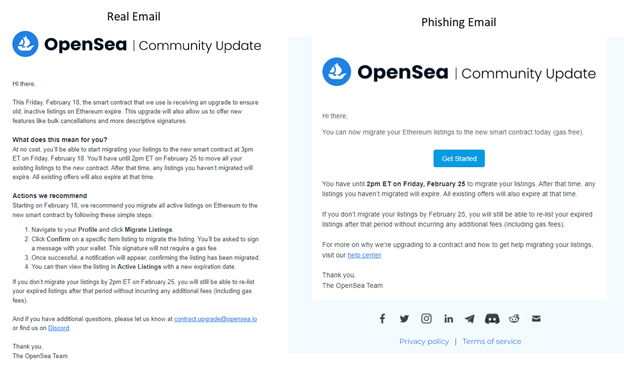
OpenSea sent an email on Wednesday the 16th letting users know anything created before Feb 18th will expire Feb 25th and need to be relisted or migrated. Users started to move their items over and then today, surprised users reported they are losing not only NFTs but ETH and other tokens during the migration process. While everyone was quick to blame OpenSea for the issue, unfortunately it had nothing to do with OpenSea. It was one of the oldest tricks in the book, Phishing.
The scammer took advantage of the OpenSea migration situation and sent out an email with a phishing link that essentially prompted the user for a signature to migrate their NFTs and what they were really signing was the ability for the scammer to take everything in the wallet. The original OpenSea email and phishing email are shown below.
While we are still learning more about the exploit, it appears that the hacker is using a signature phishing attack that was deployed several weeks ago. The interesting part is that it is interacting with an OpenSea contract that was deployed 4 years ago that provides a valid atomicMatch data. Essentially what that means is that the transaction passed the order validation by strategically using half of a valid signed order and the attacker signed the other half which used the malicious contract. To the user it just looks like a legitimate transaction due to the valid order portion. Once past the validation piece it was as simple as executing a looping script in the malicious contract to drain the wallet of all NFTs that had valid signatures on the OpenSea contract.
While on the surface it looks suspicious that contract used to “hack” was deployed weeks before the new OpenSea contract, it really has nothing to do with the new contract and everything to do with the old one and a well-planned phishing attack. It is also important to note that once the new contract was in place, this attack would no longer be possible. The scammer had to execute it ASAP or miss their opportunity.
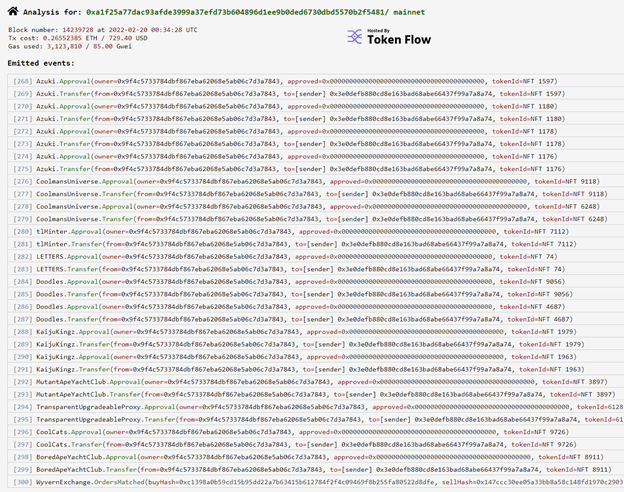
At the time of writing this, the hacker has managed to steal over 640 ETH worth $1.7m and over 30 NFTs, some worth upwards of $200k each. You can see the wallet associated with the transactions below
Wallet Address: https://etherscan.io/address/0x3e0defb880cd8e163bad68abe66437f99a7a8a74
The below screenshot shows just the initial wave of transactions, there have been more since this was taken but provides an idea for what NFTs are being stolen.
Update: In an odd turn of events, as of Monday morning, the scammer had returned many of the stolen NFTs to their owners. It is unclear why someone would go through the trouble to do this just to return it but happy for those owners to get their items back.
Just to show how good of a phishing attack this was, we found evidence of one of OpenSea’s own Software Engineer’s that fell for it. In the interest of not naming that person in this article, it was discovered by looking at the wallet transactions and aligning the wallet address which uses an ENS (Ethereum Naming Service – basically a Web3 identity to tie you to wallets) name with their Twitter/LinkedIn account.
There is always a lesson to be learned from events like this and this one proves two points: Crypto is susceptible to the same attacks that we have been dealing with for years in the Information Security field and users of crypto still do not understand the underlying technology they are using daily (i.e.. what they are signing).