By
OCD Tech
September 8, 2023
•
3
min read

SOC Reports: How to Interpret SOC Reports
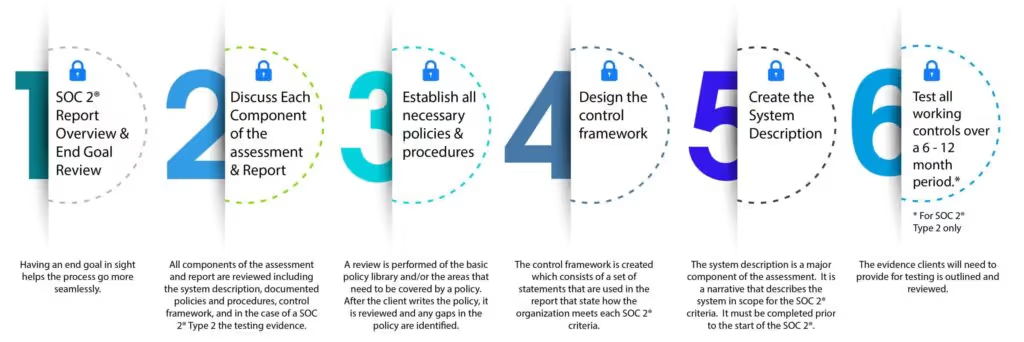
Interpreting SOC reports requires a solid understanding of the report's structure and the various sections included. Here are the key elements OCD Tech team of experts provide when reviewing SOC reports:
• Test Working Controls – The evidence that organizations will need to provide for testing is identified and reviewed.
For more information about our SOC READINESS ASSESSEMENT, visit https://ocd-tech.com/soc-2-readiness-assessment/

Audit. Security. Assurance.
IT Audit | Cybersecurity | IT Assurance | IT Security Consultants – OCD Tech is a technology consulting firm serving the IT security and consulting needs of businesses in Boston (MA), Braintree (MA) and across New England. We primarily serve Fortune 500 companies including auto dealers, financial institutions, higher education, government contractors, and not-for-profit organizations with SOC 2 reporting, CMMC readiness, IT Security Audits, Penetration Testing and Vulnerability Assessments. We also provide dark web monitoring, DFARS compliance, and IT general controls review.
Contact Info
.svg)
OCD Tech
.svg)
25 BHOP, Suite 407, Braintree MA, 02184
.svg)
844-623-8324
.svg)
https://ocd-tech.com
Follow Us
Videos
Check Out the Latest Videos From OCD Tech!
Services
SOC Reporting Services
– SOC 2 ® Readiness Assessment
– SOC 2 ®
– SOC 3 ®
– SOC for Cybersecurity ®
IT Advisory Services
– IT Vulnerability Assessment
– Penetration Testing
– Privileged Access Management
– Social Engineering
– WISP
– General IT Controls Review
IT Government Compliance Services
– CMMC
– DFARS Compliance
– FTC Safeguards vCISO