The following headline seems to show up every few weeks:
Ransomware Attack Downs Organization, Recovery Projected To Take Months.
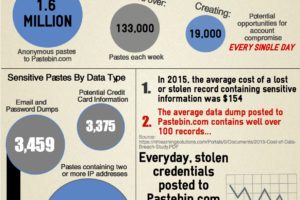
If you feel like you’re hearing about ransomware attacks more often, you’re not wrong. In fact, According to a 2021 report from cybersecurity firm SonicWall, ransomware attacks rose by 62 percent worldwide, and by 158 percent in North America alone, between 2019 and 2020. On February 9, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint advisory authored by cybersecurity authorities in the United States, Australia, and the United Kingdom. This advisory warned of an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organizations across the globe. U.S. authorities, including the FBI, the CISA, and the NSA, reported ransomware attacks against 14 of the 16 critical U.S. infrastructure sectors.
Ransomware is a type of malware that infects a computer system before propagating through the network and encrypting the victim’s files, making them inaccessible and unusable until a ransom is paid to the attacker. Ransomware is often spread through malicious websites or emails and can lead to data loss, leaks, and network outages. Ransomware attacks can also be carried out through social engineering—a technique in which attackers manipulate an individual into divulging confidential information or performing a risky action, such as clicking on a link in an email. Social engineering can also be carried out through phone calls and SMS, with both methods becoming more common for attackers in recent years.
So how can a ransomware attack be prevented?
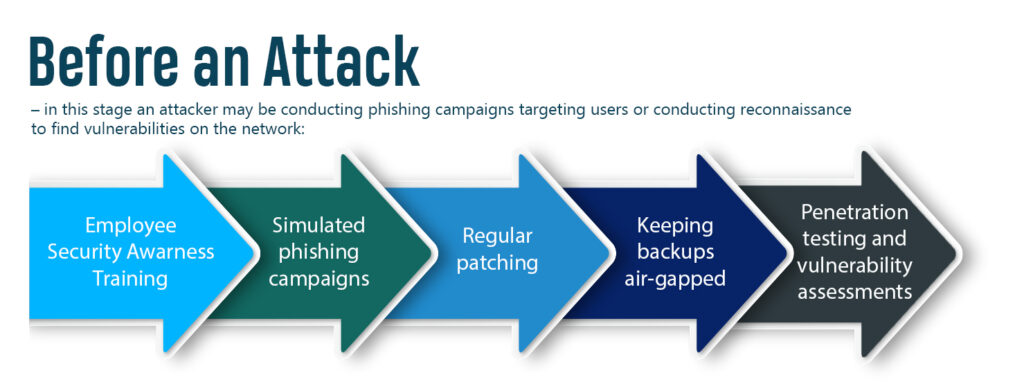
When it comes to phishing emails, employees are recommended to think before clicking, especially on attachments or links. Users should ask themselves if they were expecting an attachment from the sender and should hover over links to see exactly where the link is directing them before clicking. Employees should ensure that the sender is someone they recognize, and that the sender’s email address is valid, and not an email address made to look like a trusted sender by the attacker. Subtle differences in language or usual business operations are a telltale sign of a phishing email. When in doubt, users should alert their IT department to suspicious emails and refrain from clicking on links or opening attachments.
Simulated phishing campaigns can help educate users on recognizing phishing emails, while also providing an organization data on where they can improve. Good cyber hygiene also plays a big role in preventing ransomware attacks. Cyber hygiene includes frequent scanning, regular patching, and network segmentation to help slow the spread of a ransomware attack.
Regarding recovery from a ransomware attack, it is crucial that organizations have a comprehensive cyber response plan and keep backups to their networks air-gapped from the main network, meaning the backups are not connected and cannot be compromised by malware.
While the thought of a ransomware attack on your business can be frightening, the best defense against ransomware and other cyberattacks is vigilance and preparation. The steps you can take now can help an organization tremendously if they do fall victim to attack preventing it from compromising their network and private information.
So what can an organization do if ransomware is already present?
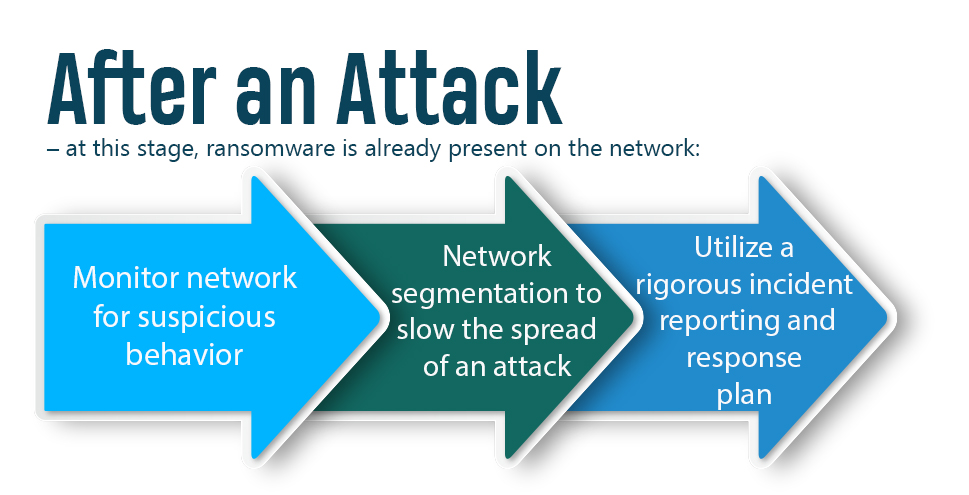
A great example of an organization’s preparedness is when a hospital in Florida recently fell victim to a ransomware attack. This Florida hospital made headlines after successfully fending off the most crippling effects of a ransomware attack through quick thinking and cooperation between IT and hospital staff. The attack targeted a third-party medical charting system used by the hospital. Jackson Hospital responded by quickly shutting down the infected systems and taking them offline. Staff disconnected from their electronic record-keeping system and pivoted to “downtime procedures,” or contingency plans that had been put in place in the event of a system outage. At the same time, IT staff worked through an inventory of their most critical computer systems to ensure that each one had not been infected before reconnecting them to the network. Communication lines between IT and hospital staff were well-established, with hospital staff noting the issue with the charting system and immediately reporting it to IT, who mobilized and responded in minutes.
What could have been a story of patient woes, massive financial losses, and diverted ambulances, turned into the story of what preparedness and early detection can do for an organization in the event of a ransomware attack.
Taking small, basic security steps today can prevent headaches and trouble down the road and can lead to a more secure organization. OCD Tech specializes in security awareness and phishing training, as well as penetration testing and vulnerability assessments to identify risk and ensure your organization is capable of negating, handling, and preparing for future threats.