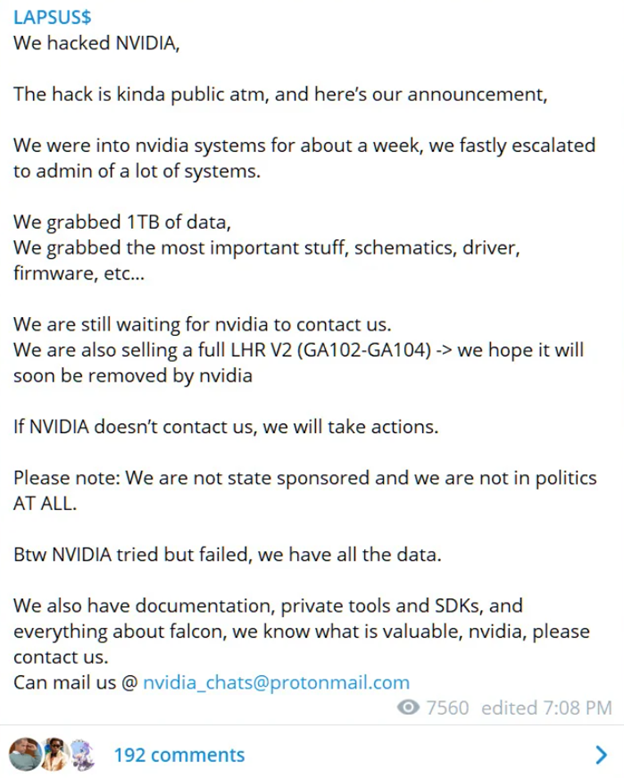
A South American-based hacking group that goes by LAPSUS$ has claimed responsibility for the recent cyberattack on Nvidia. Nvidia engages in the design and manufacturing of computer graphics processors, chipsets, and related multimedia software. They are arguably the leader in the graphics card market and, as such, work closely with a lot of software companies including Microsoft. The cyber-attack leaked the credentials of approximately 71,000 Nvidia employees which was later confirmed by the popular data-breach-monitoring website Have I been Pwned. LAPSUS$ posted the following on their twitter account:
Based on the information discovered to date, it appears that along with the 70k+ employee emails were the employees’ NTLM password hashes, many of which have been subsequently cracked and circulated within the hacking community. Fortunately, Nvidia can easily “fix” the risk involved by forcing all their users to change their passwords. Our assumption is that this has already occurred.
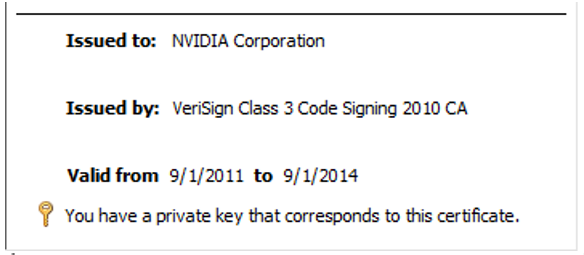
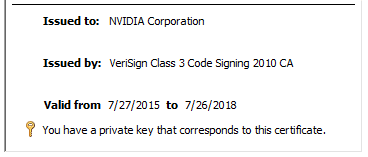
While the credentials are making most of the headlines, unfortunately this isn’t the most important part of the data breach. In a statement released by Nvidia confirming the cyberattack, they went on to say, “We are aware that the threat actor took employee credentials and some NVIDA proprietary information from our systems and has begun leaking it online.” That proprietary information they mentioned included two code-signing certificates.
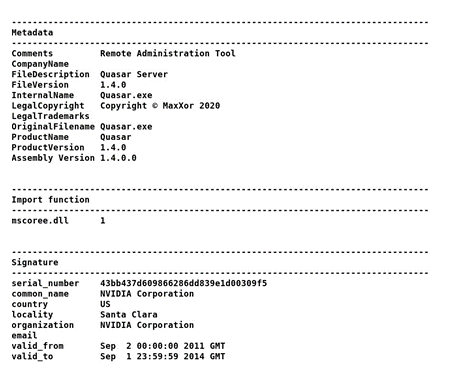
As seen above, the certificates are expired. However, Windows still allows them to be used for driver signing purposes. In most cases, Windows doesn’t care if the certificate is expired or revoked because what you see in the digital signature section of a driver is not something that the kernel checks for when determining whether to load a driver. When it says that a certificate is explicitly revoked, that is what “WinVerifyTrust” is returning and not what the kernel cares about (the WinVerifyTrust function performs a trust verification action on a specified object. More on WinVerifyTrust can be found on Microsoft’s Website). That said, because the kernel accepts the expired certificate, most antivirus companies out there do not flag this as a threat.
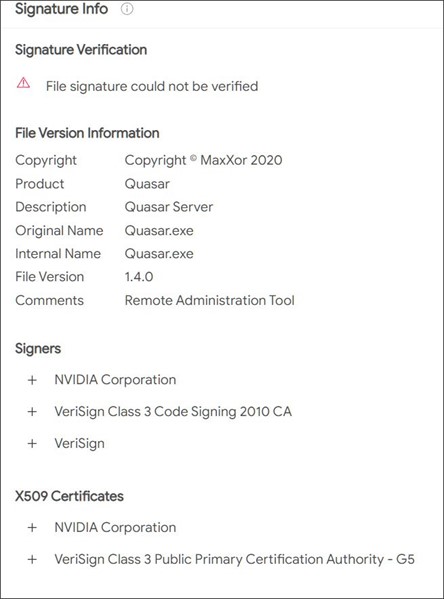
We are already seeing multiple instances of malware utilizing these signed driver certificates in order to bypass antivirus. Thanks to @vxunderground on Twitter, we were able to obtain samples of the malware being used in Quasar.exe which is a Remote Administration Tool. We can see it has a valid signature, and the signers and certificate are Nvidia Corporation.
As you can probably imagine, this is just the beginning of the abuse of these certificates. Unfortunately, we likely won’t see a fix in the form of Microsoft adding these to their certificate revocation list anytime soon. Doing so would most likely cause legitimate Nvidia drivers to be blocked, too. Conversely, there is a way that organizations can combat it. David Weston, Director of Enterprise and OS Security at Microsoft, Tweeted that admins can configure Windows Application Control policies to control what Nvidia drivers can be loaded.
If there was ever a time to be vigilant on what you click or install, now is the time.