By
OCD Tech
February 9, 2022
•
2
min read

The Federal Trade Commission (FTC) recently released their Final Rule to amend the Standards for Safeguarding Customer Information. The final Rule includes 5 primary modifications to the existing Safeguards Rule. The Final Rule adds provisions designed to provide covered financial institutions with more guidance on how to develop and implement an information security program, adds provisions designed to improve accountability of financial institutions who are trusted with customer information, exempts some financial institutions from certain requirements if they hold records for less than 5,000 customers, expands the definition of “financial institutions” to include “finders”, and finally, defines several terms and providers related examples for the Rule’s requirements.
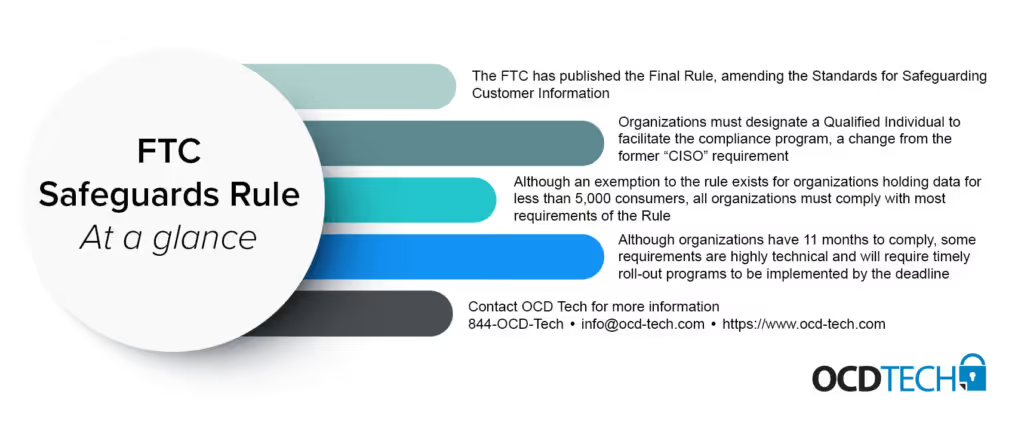
Many automotive dealerships may question how this applies to them. Afterall, automotive dealerships are not formal banking institutions. However, many automotive dealerships provide financial services to customers, such as automotive loans. These types of continuing financial relationships are what trigger the applicability of the FTC Safeguards Rule.
Included in the amendment to the Safeguards Rule is the change from requiring organizations to have a Chief Information Security Officer (CISO) to a Qualified Individual. Now, organizations must designate a Qualified Individual to facilitate their information security and compliance program. This Qualified Individual must be someone whom the organization can prove is trained in, and understands, information security. Indeed, larger dealerships may elect to hire someone full-time for this role. However, smaller dealerships may already have someone on staff who can fulfill this role in addition to their other job duties. Organizations may also, if they lack this type of talent on their teams, outsource this requirement to a third-party.
A Virtual CISO (hereafter vCISO) may be leveraged by a dealership to provide objective information security guidance and leadership. In some ways, hiring a vCISO can be more cost prohibitive than hiring a dedicated full-time resource, for many vCISO offerings are facilitated via retainer.
No matter the avenue for establishing a Qualified Individual, it is imperative that organizations do this first, for all subsequent requirements must be facilitated by that Qualified Individual. The other requirements established by the Final Rule include:
Built into the Safeguards Rule is an exemption for financial institutions that hold data for less than 5,000 customers. OCD Tech reached out personally to the FTC to clarify the meaning of this exemption. In their response, the FTC clarified that the exemption for less than 5,000 consumers is total, not annual. Meaning, at any point in time the organization must retain less than 5,000 customers data, not just annually.
This exemption absolves organizations of responsibility for the following requirements:
To be clear, all financial institutions are responsible to meet all other requirements of the Rule. This means that for financial institutions, including automotive dealers that hold data for even 1 customer, must implement data security controls within the Rule such as encryption, multi-factor authentication, and access controls.
The Final Rule is effective 10 January 2022 and organizations have until 9 December 2022 to comply with all parts of the Safeguards Rule. Organizations may find that they can meet these controls in-house. Others may determine that they require assistance from a third-party to establish and maintain their compliance program.
With that in mind, certain requirements of the Rule will very likely require the assistance of a third-party. Most notably, the requirements for continuous monitoring or penetration testing and logging will not only take the longest to implement (assuming the organization has not yet implemented these controls) and are very likely to require facilitation by a third-party expert. With just 11 more months to implement these requirements, all organizations should be considering their avenue for compliance.

Audit. Security. Assurance.
IT Audit | Cybersecurity | IT Assurance | IT Security Consultants – OCD Tech is a technology consulting firm serving the IT security and consulting needs of businesses in Boston (MA), Braintree (MA) and across New England. We primarily serve Fortune 500 companies including auto dealers, financial institutions, higher education, government contractors, and not-for-profit organizations with SOC 2 reporting, CMMC readiness, IT Security Audits, Penetration Testing and Vulnerability Assessments. We also provide dark web monitoring, DFARS compliance, and IT general controls review.
Contact Info
.svg)
OCD Tech
.svg)
25 BHOP, Suite 407, Braintree MA, 02184
.svg)
844-623-8324
.svg)
https://ocd-tech.com
Follow Us
Videos
Check Out the Latest Videos From OCD Tech!
Services
SOC Reporting Services
– SOC 2 ® Readiness Assessment
– SOC 2 ®
– SOC 3 ®
– SOC for Cybersecurity ®
IT Advisory Services
– IT Vulnerability Assessment
– Penetration Testing
– Privileged Access Management
– Social Engineering
– WISP
– General IT Controls Review
IT Government Compliance Services
– CMMC
– DFARS Compliance
– FTC Safeguards vCISO