By
December 4, 2019
•
8
min read
Have you ever wondered if there was an easier way to respondto audit requests or search your Active Directory for privileged access?PowerShell’s Active Directory module is the answer. Many people believe thatyou need to be a scripting expert to even use the PowerShell terminal, but witha little practice, you will be querying your Active Directory with PowerShellin no time.
In PowerShell, a cmdlet (command-let) is a lightweight command that is used in Windows. When using cmdlets, you have the option to use a cmdlet parameter. Cmdlets can also accept parameters that allow you to further refine and specify which results you want the cmdlet to return. Listed below are some of the most useful Active Directory cmdlets that PowerShell has to offer.
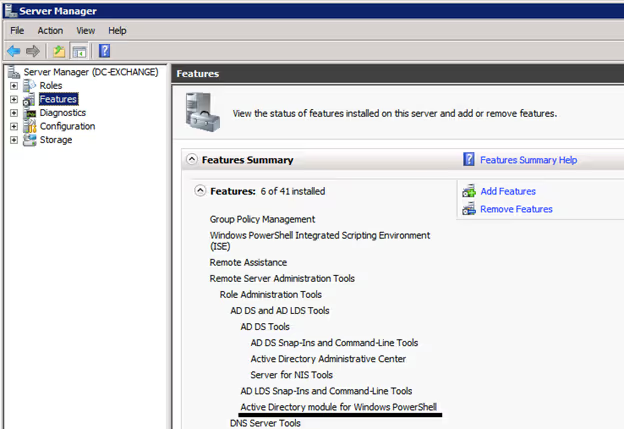
Before diving into the Active Directory PowerShell commands, please make sure you have the correct module installed. The Microsoft Remote Server Administration Tools (RSAT) contain the Active Directory module for PowerShell. To find out if RSAT is installed, launch the Server Manager MMC, and click the “Features” section. Look for the “Active Directory Module for Windows PowerShell”. Once enabled, you’ve unlocked the power to dig into Active Directory.
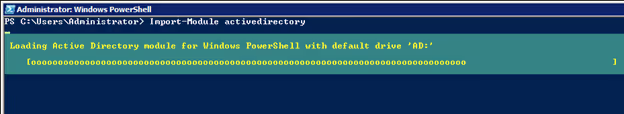
This command starts the PowerShell Active Directory module and loads all cmdlets. If you do not have this module pre-installed, please reach out to your system administrator for help with installing the correct Remote Server Administration Tools (RSAT).
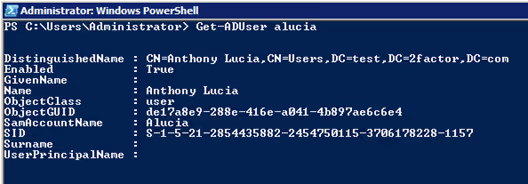
Get-ADUser is used to find either one specified user or multiple users. The Identity parameter will return one user, while the Filter parameter can use a wildcard to return a selection of users. The Properties parameter is also useful. To view all properties that a user object has, specify a wildcard by inserting an asterisk. Some of the more informative properties are SamAccountName, Name, EmailAddress, LockedOut, Created, and LastBadPasswordAttempt.
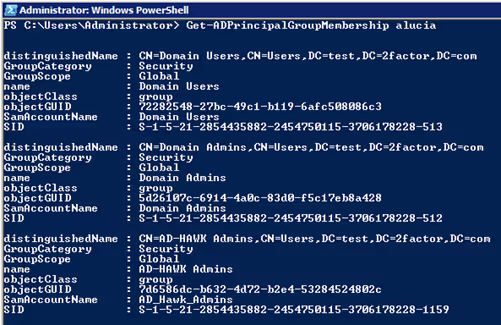
After finding out that a user object exists, you probably want to know where it has access. The user could have direct access to a server or to an application, but there is also the chance that the user is a member of a group that has privileged access. Get-ADPrincipalGroupMembership gives an object-based output of the users Active Directory group membership. The simplified version of this is the Get-ADUser property called MemberOf, but this limits the results to only the distinguished LDAP name. With Get-ADPrincipalGroupMembership, you will receive more properties for that group, which can be queried and filtered for a refined search.
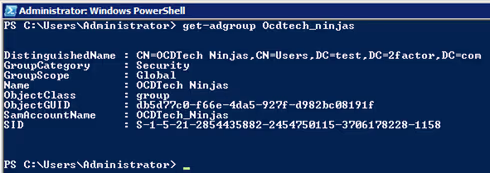
This cmdlet is used to pull multiple groups from the Active Directory. Get-ADGroup uses parameters similar to Get-ADUser, but focused more on relating to the group object. The Identity parameter returns the attributes of one group. The Filter parameter will return multiple group objects based on the query. Specifying * will return all groups in the domain. The Properties parameter returns group properties. To select all properties, specify *. Make note of SamAccountName, ManagedBy, and whenChanged. For audit purposes, whenChanged is important. This property is updated when a new user is added or removed from a group, so it would be a quick indicator of any new privileged access being granted.
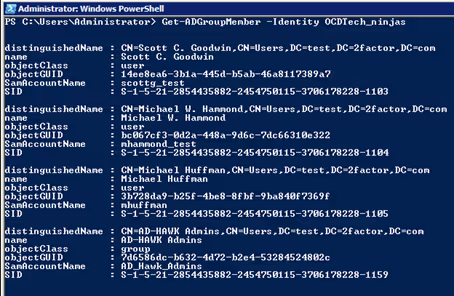
After finding a group, you can run the cmdlet Get-ADGroupMember. Get-ADGroupMember returns all the members of an Active Directory group (group members are either users, other groups, or computers). It is possible to get these same results from the Get-ADGroup property Members, but the property from Get-ADGroup only provides the distinguished name through LDAP.
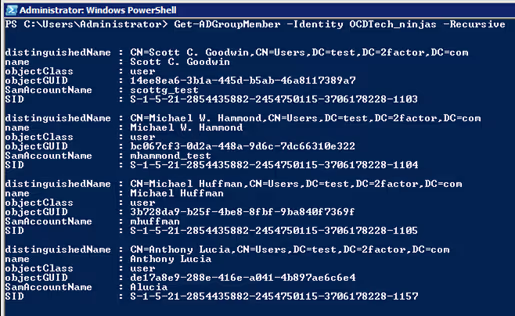
Notice how there is the group “AD-HAWK Admins” within-group “OCDTech_Ninjas”. Unless you use a parameter to help you dig a little deeper, you will not be able to see all the members that have access to a group, due to members that may have indirect access. The Recursive parameter will search a group and pull all direct and indirect members of that group. For example, if the group “OCDTech_Ninjas” contains three users, but also contains the group “AD-HAWK Admins,” and “AD-HAWK Admins” contains the user “ALucia,” the cmdlet will return all the direct members within “OCDTech_Ninjas” and “ALucia.” Users within “OCDTech_Ninjas” are direct members of the group, but user “ALucia” is an indirect member.
Answering audit requests and monitoring privileged access within Active Directory is approachable and achievable through basic PowerShell commands. Although we have only scratched the surface of what the Active Directory PowerShell Module can do, these commands above are core cmdlets that you should use frequently when dealing with Active Directory. By utilizing the tools in this paper, the reader should have the skills to navigate through basic Active Directory with ease.

Audit. Security. Assurance.
IT Audit | Cybersecurity | IT Assurance | IT Security Consultants – OCD Tech is a technology consulting firm serving the IT security and consulting needs of businesses in Boston (MA), Braintree (MA) and across New England. We primarily serve Fortune 500 companies including auto dealers, financial institutions, higher education, government contractors, and not-for-profit organizations with SOC 2 reporting, CMMC readiness, IT Security Audits, Penetration Testing and Vulnerability Assessments. We also provide dark web monitoring, DFARS compliance, and IT general controls review.
Contact Info
.svg)
OCD Tech
.svg)
25 BHOP, Suite 407, Braintree MA, 02184
.svg)
844-623-8324
.svg)
https://ocd-tech.com
Follow Us
Videos
Check Out the Latest Videos From OCD Tech!
Services
SOC Reporting Services
– SOC 2 ® Readiness Assessment
– SOC 2 ®
– SOC 3 ®
– SOC for Cybersecurity ®
IT Advisory Services
– IT Vulnerability Assessment
– Penetration Testing
– Privileged Access Management
– Social Engineering
– WISP
– General IT Controls Review
IT Government Compliance Services
– CMMC
– DFARS Compliance
– FTC Safeguards vCISO