On May 14th, as part of Patch Tuesday, Microsoft announced a high-risk vulnerability (CVE-2019-0708) that exists in their Remote Desktop Protocol (RDP). The vulnerability, now known as BlueKeep, affects Windows Server 2003, Windows XP, Windows 7, Windows Server 2008, and Windows Server 2008 R2. The BlueKeep vulnerability allows unauthenticated attackers to execute arbitrary code on vulnerable systems. If that isn’t scary enough, the vulnerability is also “wormable”. “Wormable” vulnerabilities allow for the automatic detection and exploitation of other vulnerable systems that are visible from the initially targeted system. To put this in perspective, the most recent “wormable” vulnerability was the MS17-010 (ETERNALBLUE) vulnerability which was exploited to spread WannaCry ransomware across the globe.
Here at OCD Tech, we are anticipating the widespread exploitation of the BlueKeep vulnerability. Over the past few days, we have been monitoring the Greater Boston Area for systems that may be vulnerable to attack. With the use of Shodan, a search tool that indexes everything connected to the internet, we were able to collect a dataset of all systems with open RDP ports (port 3389). The dataset contains information including IP address and location for each of the 3,875 potential target systems. From the dataset we were able to generate a heatmap to better visualize the relative concentrations of potentially vulnerable systems:
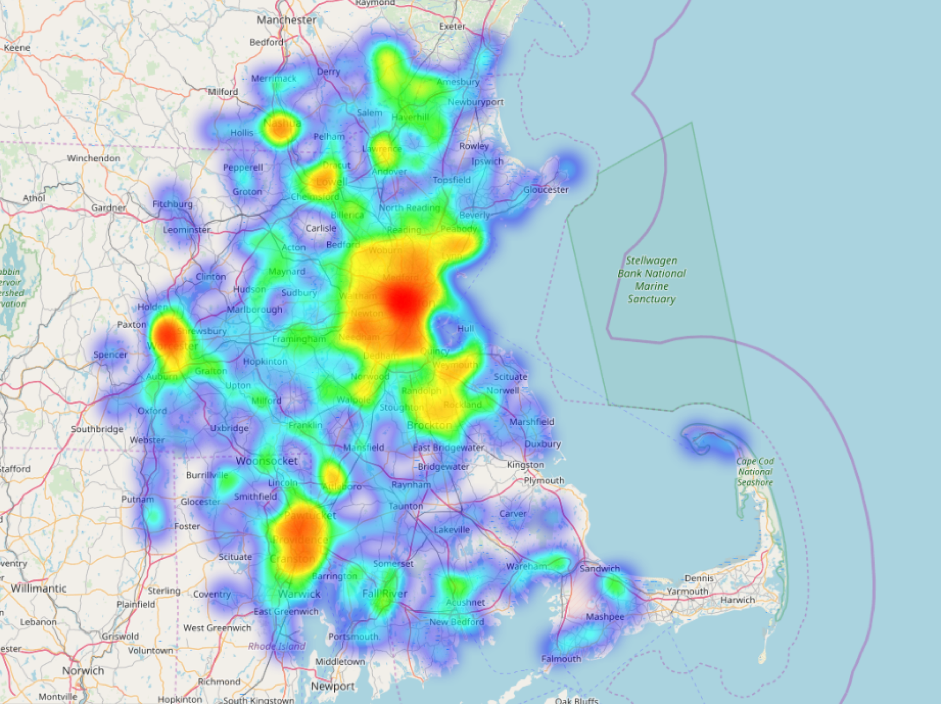
From the heatmap, it is easy to see that the Greater Boston Area is home to many potentially vulnerable systems. Without performing a more invasive scan of each system, it’s impossible to tell if these systems are truly vulnerable, however, they are exposing the RDP service to the internet, and therefore may become potential targets over the coming weeks. Attackers are already scanning the internet trying to identify exposed RDP ports. A number of proof-of-concept scanners and exploits are becoming available, which is a sure sign of impending attacks. If you are worried about your systems being compromised, OCD Tech recommends that you do the following:
- Ensure that no RDP services are directly exposed to the internet. RDP services which are required remotely should first leverage a VPN connection or other tunnel to protect internal systems from direct remote compromise.
- Enable Network Level Authentication via GPO for all RDP services. There is partial mitigation on affected systems that have Network Level Authentication (NLA) enabled. The affected systems are mitigated against ‘wormable’ malware or advanced malware threats that could exploit the vulnerability, as NLA requires authentication before the vulnerability can be triggered. However, affected systems are still vulnerable to Remote Code Execution (RCE) exploitation if the attacker has valid credentials that can be used to successfully authenticate.
- Apply the Microsoft provided patches as soon as possible, starting with systems which host critical services or sensitive data.
- If patches cannot be applied in a timely manner, disable RDP services entirely on vulnerable systems until the patch can be applied, especially on critical systems.



