One of the most accredited forms of validation for a citizen’s identity is a Social Security Number. A Social Security Number is a significant piece of government-issued identification in the United States. When this information is compromised it can lead to serious problems where an individual can use a stolen Social Security Number, along with a name, to impersonate another citizen.
A citizen may never know that their Social Security Number has been compromised, but even if they do, it can still take several months (or years) to obtain a new one. When a Social Security Number is compromised, whether it’s known or not, a malicious entity can leverage it to impersonate a citizen to achieve various goals including utilizing their health care and opening credit lines.
The most important steps to take, once it is believed that a Social Security Number has been compromised, is to first file an identity theft report with the local police. Secondly, place a fraud alert on your credit file which will be displayed on a credit score to indicate a potential identity theft has occurred. This can be done by contacting a credit reporting agency such as Equifax, TransUnion, or Experian.
Identity fraud is more common than many citizens believe. A study done by Javelin Strategy and Research released its findings in February of 2018 revealing that the rate of fraud victims per year is increasing.
Many incidents of identity fraud can be traced back to data breaches of major companies that deal with and store sensitive information of citizens. A recent example of a large amount of Social Security Numbers being leaked is the Equifax data breach discovered in July of 2017. This breach has a reported Number of 145.5 million who were affected. Due to this breach, many citizens have their Social Security Numbers being sold online for anyone to purchase or being shared freely by malicious entities.
When hackers and identity thieves look to share information or advertise information they’re looking to sell, they migrate towards websites that allow for anonymous posting. The most commonly known, and utilized, are Pastebin, Gist, and Slexy. At OCD-Tech we have been developing a tool that constantly scrapes these anonymous posting sites for sensitive information, one of which is Social Security Numbers.
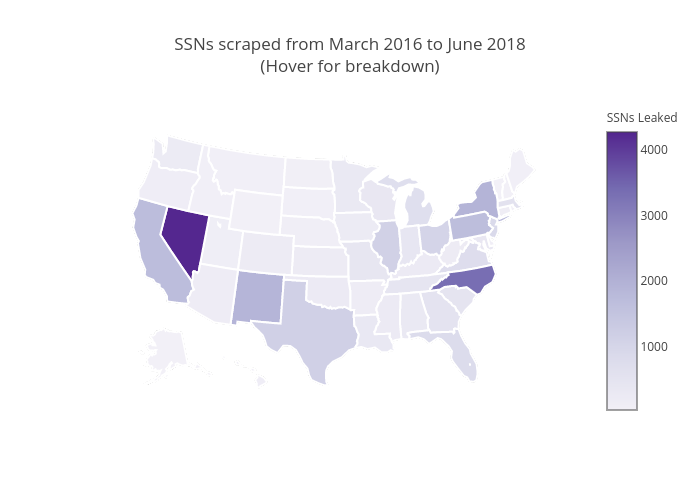
We were able to capture 28,260 unique Social Security Numbers over about a year and 3 months. That comes to an average of 239 Social Security Numbers per week and 1,047 Social Security Numbers per month. The below image indicates a mapping of Social Security Numbers we found to the corresponding state which they were assigned from. (This practice was discontinued after June 2011, so not all found Social Security Numbers may be mapped)
https://plot.ly/~DanScrapy/20/ssns-scraped-from-march-2016-to-june-2018-hover-for-breakdown/
Protecting yourself from identity theft is a losing battle. The majority of Social Security Numbers compromised are due to breaches, which means there isn’t much to be done by citizens to protect their Social Security Number. The best that can be done is to monitor your credit report and stay up-to-date on current events involving breaches of sensitive information, especially those regarding companies you’ve given your Social Security Number to. Performing these actions can allow a citizen to report a potential threat quickly and mitigate damages. Alternatively, there are companies that provide identity theft monitoring as a service.
This project was created by Daniel Bohan and Daniel Kelly.